
Most compliance programs do not fail because controls are poorly designed. They stumble because proving that controls worked requires chasing busy colleagues for screenshots, exports, and sign offs. If your team spends the last week of every quarter collecting evidence, this guide is for you. Below is a practical roadmap to automate evidence collection for compliance controls, preserve integrity of records, and get faster responses from the people you depend on.
The real reason evidence collection breaks down
Compliance teams typically run on email, spreadsheets, and shared drives. That makes sense at small scale, but it does not survive audits, turnover, or regulatory scrutiny. When evidence is scattered, you face three recurring problems. First, integrity, because it is hard to show where a file came from and whether it changed. Second, latency, because each request requires back and forth coordination. Third, fatigue, because colleagues receive vague asks with unclear deadlines.
Automation fixes these by capturing evidence at the source, linking it to the control it supports, and centralizing it in an auditable repository with clear ownership and due dates.
What counts as evidence and who is asking for it
What you must retain depends on your regulatory perimeter and your compliance policy. Here are examples aligned to common frameworks for mid market organizations.
- Loi Sapin II expects documented anti bribery and anti corruption measures, including risk mapping, training, third party due diligence, gifts and hospitality records, and internal controls.
- ISO 37001 requires documented information for anti bribery management systems, such as training completion, due diligence outputs, approvals, investigations, and corrective actions.
- Spanish UNE 19601 and UNE 19603 standards expect evidence that criminal compliance and antitrust control activities were designed, implemented, and monitored.
- AML frameworks require customer due diligence files, risk scoring and reviews, transaction monitoring alerts and dispositions, and record keeping for specified periods.
- The EU AI Act introduces documentation and logging obligations for high risk AI systems, including risk management files, data governance records, incident logs, and human oversight procedures.
Across these frameworks, evidence is any element that demonstrates a control was performed as designed, by the right person, at the right time. The quickest path to automation is to map each control to the system that already produces that element.
Choose the right controls to automate first
Start with controls that are frequent, high volume, or cross functional. These usually generate the largest time savings and adoption gains.
- Mandatory compliance training and attestations, for example anti bribery, antitrust, code of conduct, conflicts of interest.
- Third party due diligence, including risk tiering, screening hits, approvals, and re assessments.
- Gifts, hospitality, donations, and sponsorship approvals and registers.
- AML customer due diligence and periodic reviews if you are in scope.
- Procurement and finance approvals that evidence segregation of duties.
- Technical documentation and logs for high risk AI systems, if applicable.
Automating these six will usually eliminate most quarter end chases. Add bespoke or sector specific controls once you have proven the pattern.
Build your evidence catalog
Create a simple catalog that links every control to the evidence that proves it, the system of record, and a collection rule. Treat it as your blueprint for automation.
Control | Frameworks most aligned | Evidence to capture | Source system and collection rule |
|---|---|---|---|
Anti bribery training completion | Loi Sapin II, ISO 37001, UNE 19601, UNE 19603 | Completion status, date, score, attestation, manager confirmation for critical roles | Learning management system, nightly API export keyed by employee ID; join to HRIS roster for population coverage |
Third party due diligence | Loi Sapin II, ISO 37001, UNE 19601, AML where relevant | Risk tier, screening reports, hit resolution, approval record, re assessment date | Vendor portal or due diligence tool, event driven webhook on status change; archive PDFs and JSON payloads |
Gifts and hospitality | Loi Sapin II, ISO 37001 | Register entry, amount, recipient, justification, pre approval where required | Expense tool or simple form, on submit store normalized record and attachment; auto apply thresholds by country |
Conflicts of interest | Loi Sapin II, UNE 19601 | Annual declaration, changes, approvals | Pre filled form sent to in scope roles each year; auto remind until completion; signed PDF and data extract |
AML CDD and reviews | AML | KYC file index, beneficial ownership, risk score, reviewer, next review date | KYC platform, nightly API export of metadata and links; archive key docs, hash and timestamp |
AI system risk management | AI Act | Risk register entries, testing logs, incidents, sign offs | Model registry or ticketing, webhook on model promotion or change request; collect artifacts and link to system ID |
Use controlled vocabularies and unique IDs so you can tie evidence back to a control, process, system, third party, or individual without manual reconciliation.
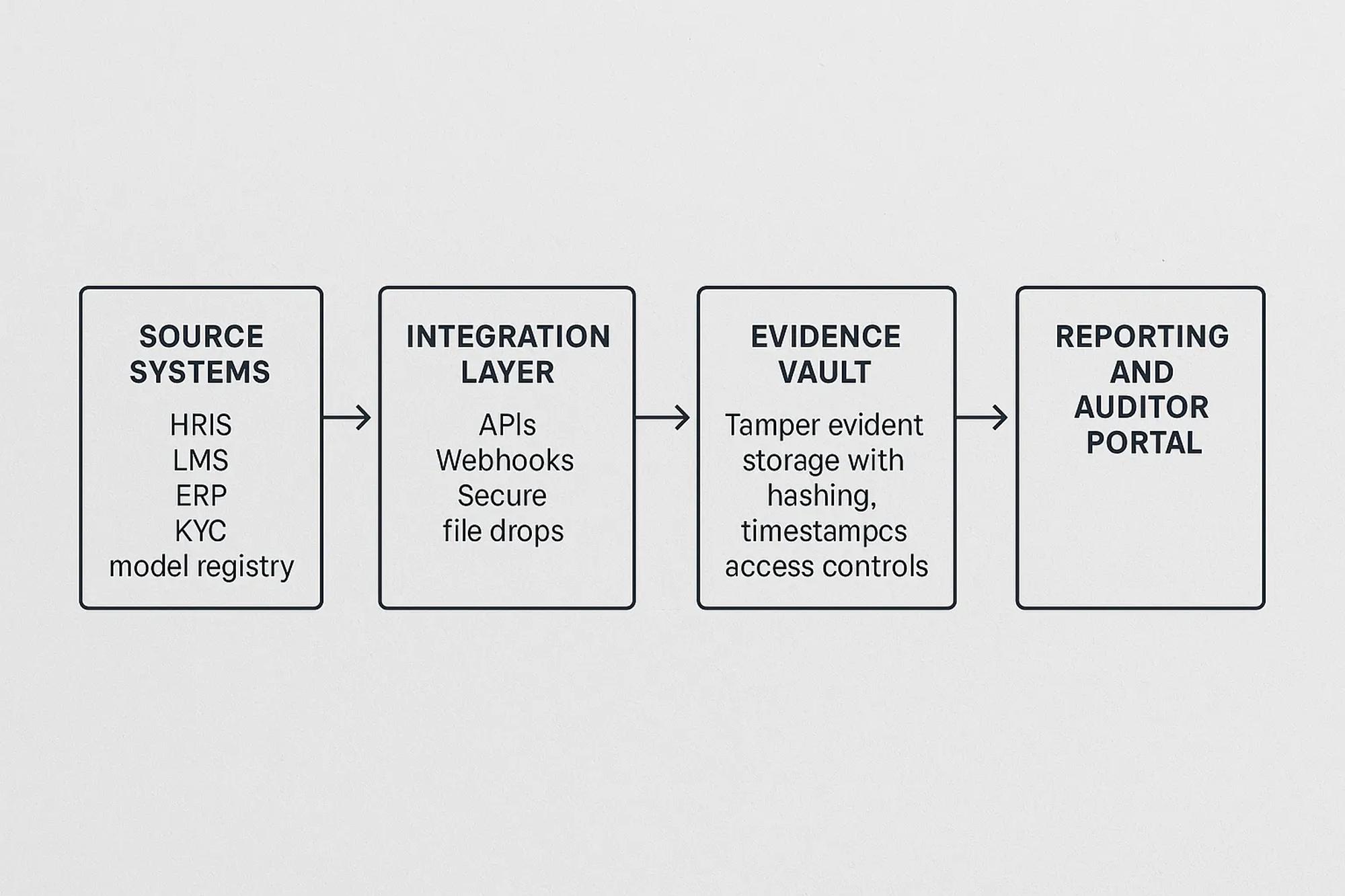
Five patterns that automate evidence collection
1 System to system extraction
Use APIs, webhooks, or secure file drops to pull evidence from the system of record. Prefer scheduled jobs for stable datasets and event driven webhooks for status changes. Minimize transformation to preserve provenance. Store the raw payload alongside any human readable rendering.
Good candidates are LMS completions, ticketing approvals, procurement sign offs, KYC review statuses, and model promotion logs. Avoid RPA for core evidence when reliable APIs exist. RPA can support edge cases but increases brittleness.
2 Pre filled attestations instead of blank forms
When you cannot collect evidence passively, make the task easy. Pre populate forms with what you already know, for example name, role, manager, last training date, third party details, or prior declarations. Then ask for a simple confirm or update. This reduces cognitive load and error rates.
3 Event driven control triggers
Tie control evidence to business events. New hire triggers required trainings and policy acknowledgements. New vendor triggers due diligence. New AI model version triggers a risk review. Event driven flows shorten cycle time and improve coverage because tasks appear when they are most relevant.
4 One click approvals with audit trails
For approvals, route a concise summary to the approver and capture their decision with time, identity, and context. Do not make approvers hunt for information. Include threshold logic, country rules, and conflict checks in the workflow so reviewers only see decisions that truly need human judgment.
5 Auto classification and linkage
If your platform supports it, use AI or rules to auto classify incoming files and emails, detect missing fields, and link artifacts to the correct control and entity. Always keep a verifiable audit trail that shows suggested labels, human overrides, and timestamps.
Make people actually answer
Automation reduces manual effort, but you will still need timely inputs from control owners and subject matter experts. Response rates improve when you change the ask, the channel, and the incentives.
- Ask one thing at a time. Replace vague requests with a single, unambiguous action. For example, Review the attached gifts register entry for ACME Ltd, amount 250 EUR. Approve or reject by Friday.
- Use the channels people already use. Deliver tasks where work happens, for example email or calendar invites. If your internal policy allows, mirror reminders in collaboration tools to shorten the path to action.
- Set short deadlines with automatic, polite nudges. A three day window with daily reminders outperforms a two week window with one reminder.
- Escalate predictably. After two nudges, notify the manager with the original context. Consistency changes behavior faster than ad hoc chasing.
- Pre fill and preview. Show exactly what will be recorded and let the user correct it. The credibility of the record increases when recipients can see and fix the data tied to their name.
- Make progress visible. A simple dashboard that shows completed versus outstanding tasks by team creates healthy peer pressure, especially when leadership reviews it monthly.
Here is a request template you can adapt.
Action needed by Friday 5 pm: approve gifts register entry for ACME Ltd, amount 250 EUR, offered on 3 Oct. Decision required under the Anti Bribery Policy. Click Approve or Reject. If no action by the deadline, this will escalate to your manager. Questions to compliance at [insert compliance e-mail address]
The key is specificity, one click action, and a clear consequence for inaction.
Protect integrity, privacy, and retention
Evidence is only as strong as its chain of custody. Treat your evidence vault like a financial ledger.
- Preserve provenance. Keep raw source files or payloads, compute a hash at ingestion, and timestamp each artifact. Never overwrite. Append new versions with deltas and keep an immutable audit log of changes.
- Control access. Apply least privilege so that only control owners and auditors can view sensitive artifacts. Use role based access and time bound access grants for external auditors.
- Minimize personal data. Collect only what is necessary to prove the control. Mask or tokenize where possible, and avoid storing full documents when metadata suffices.
- Respect retention rules. Align retention with statutory or contractual requirements, which may differ across AML, employment, or product safety regimes. Automate purge on schedule and record the deletion.
- Govern cross border transfers. If evidence crosses borders, document your transfer mechanism and supplier obligations in your vendor due diligence and data processing agreements.
A 90 day pilot plan
You can stand up a first phase in one quarter without boiling the ocean.
- Weeks 1 to 2, scope. Inventory your top 10 controls by volume and audit criticality. For each, note the evidence, source system, owner, population in scope, and due date logic.
- Weeks 3 to 4, design. Build your evidence data model, naming conventions, and retention rules. Define event triggers and due date formulas. Draft notification templates and escalation policy.
- Weeks 5 to 8, integrate and pilot. Connect two systems, for example LMS and vendor due diligence. Configure two declarative forms for conflicts and gifts. Pilot with one business unit. Track cycle time, completion rate, and data quality.
- Weeks 9 to 12, harden and extend. Add a third system or control, implement dashboards, finalize access controls, and document operating procedures. Collect feedback, tune thresholds, and prepare for auditor walkthroughs.
By day 90, you should have visible reduction in manual chases and a reusable pattern to roll out across the control library.
Measure what matters
Good metrics prove that automation works and spotlight where to improve.
- Coverage, percentage of in scope population with evidence captured per control and period.
- Cycle time, median time from trigger to evidence captured.
- First time right rate, percentage of artifacts that require no rework due to missing fields or misclassification.
- Response rate, percentage of tasks completed by the first reminder and before escalation.
- Exception volume, number of policy exceptions raised and resolved.
- Auditor pull time, average time to produce a complete evidence set for a sampled control.
Track by business unit and control owner. Share the dashboard monthly with leadership to reinforce tone at the top.
Common pitfalls to avoid
- Automating a broken process. Standardize your control steps and fields before you wire them into a workflow.
- Letting every team design its own forms. Use a common schema so you can aggregate and report. For example, standardize third party categories and risk tiers.
- Over collecting. If a simple log entry suffices, do not demand full PDFs from 20 regions.
- Ignoring change management. Publish a calendar of compliance asks, cadence, and the expected time commitment. Predictability increases cooperation.
- Missing the legal basis. For attestations that include personal data, document your purpose, legal basis, and retention schedule up front.
Where Naltilia fits
Naltilia was built to remove the busywork from compliance. The platform supports automated data collection and compliance workflow automation, so evidence flows from systems and people into one place with clear ownership and timelines. Combined with regulatory risk assessment, remediation tracking, and tailor made policies, Naltilia helps compliance teams scale without adding headcount.
If you want to replace quarter end chases with a defensible, automated process for collecting evidence of your compliance controls, talk to us at Naltilia. We can help you prioritize high value controls aligned to Loi Sapin II, ISO 37001, UNE 19601 and 19603, AML obligations, and the AI Act, then pilot automation that your auditors and your colleagues will appreciate.

